Setup
Recommendation: Have all windows endpoints registered and reporting to the WSUS server.
Do the following in order (note: the connector must be deployed on the WSUS server before it can be added as a discovery source)
- Disable IPv6 on WSUS server
- Add the WSUS server to JetPatch
- Add and assign an administrative account to the WSUS server
- Deploy the JetPatch connector on the WSUS server
- Add the WSUS discovery source
Note: You can only add one WSUS server as a discovery source to JetPatch. For more WSUS servers use a primary-replica setup.
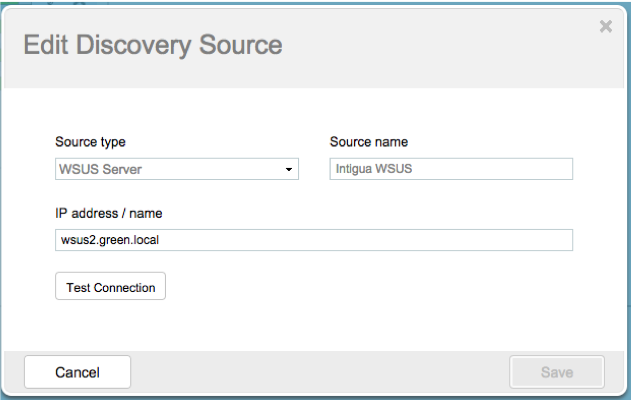
Post-Steps
Within 20 minutes, all machines reporting to WSUS should be reporting to JetPatch. From there, you can do the following
- Add and assign an administrative account to the Windows endpoints
- Deploy the JetPatch connector on the Windows endpoints
Certificates (Optional)
Note - In managed environments, we recommend deploying the following certificates (if you need them) using the GPO capabilities. If some of your endpoints are not managed or you prefer not to do it via the GPO you can use the instructions below:
WSUS Certificate
To enable secure communication between WSUS and the Windows endpoint you need to install a certificate on the endpoints.
You can deploy the certificate by using:
- GPO (see article)
- Intune (see article)
- Built-in JetPatch Script (WSUS SSL Certificate) - the certificate should be located in a path described in the wsus-certificates.path configuration in the intigua.properties file. The default location is - /usr/share/intigua/wsus-certs.
- Connector MSI Installation - the certificate should be located in a path described in the wsus-certificates.path configuration in the intigua.properties file. The default location is - /usr/share/intigua/wsus-certs.
3rd Party Patching Certificate
To patch 3rd party updates in your Windows environment there is a need for another certificate to be installed in the endpoints.
You can deploy the certificate by using:
- GPO
- Built-in JetPatch Script after Connector deployment (see instructions below)
- Connector MSI Installation
Note: For non-GPO deployment, the full certificate file path should be described in the third-party-certificate.path configuration in the intigua.properties file.
Install 3rd Party Certificate using JetPatch Built-in Script
To install the 3rd Party certificate using JetPatch capability of running a task on the endpoint, you need to create a task with the right values from the built-in script.
-
Preparation:
- Put the 3rd party certificate in the JetPatch Server and add the following parameter to the intigua.properties file (Replace <FILE_PATH> with the full path of the certificate)
third-party-certificate.path=<FILE_PATH> -Example: third-party-certificate.path=/usr/share/intigua/3dpp/3dpp.crt- restart tomcat(systemctl restart tomcat) For versions prior to 5.0 and restart intigua-main(docker restart intigua-main) for post 5.0 to apply the new configuration.
-
Create a Task:
- Go to "System -> Tasks" and click on "+ CREATE TASK" button
- Fill the "Task Name" and Description as you want
- On the right of the page, go to the "Execution" tab -
- Task Source = Both
- Script = "Third-party patching certificate Windows"
- Execution Type = "Power shell script"
- Execution Command = ".\@file @Username @API_Key @URL"
- Switch to the "Parameters" tab -
- API_Key = generate API permission and copy the generated key into the "API_Key" parameter.
- URL = the full JetPatch URL with hostname or IP (example - "https://30.30.201.55").
- Username = the username that was generated in the API_Key.
- Click on "SAVE TASK".
After the task is saved, you can select the required endpoints in "Endpoints" -> "Management" and run the task on them.
Related Articles
Comments
0 comments
Please sign in to leave a comment.