Once JetPatch Manager is able to connect to endpoints, it needs to be able to log into them to manage their management stacks. For this, it needs user accounts with administrative permissions over the endpoints.
You need to provide one or more user accounts, and then to assign an account to each machine. The provided accounts remain available for assignment to future endpoints; you can change an account's password, and the new password will then be automatically used for all endpoints to which the account is assigned.
If you try to perform an endpoint action from the Console, and JetPatch Manager doesn't have an account for the endpoint, you'll be prompted to assign one. For non-attended endpoint actions (REST API actions and policy-based provisioning) to endpoints that don't already have assigned accounts, you can configure a policy for default accounts.
-----------
Providing Endpoint User Accounts
To provide endpoint user accounts:
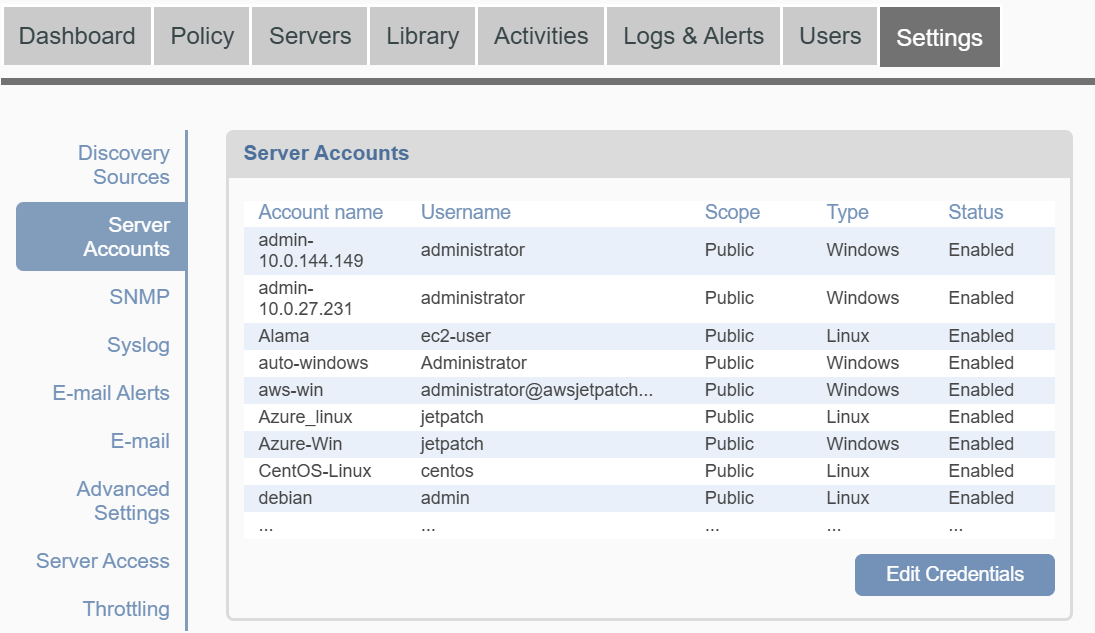
- Log in as an Administrator, and go to Settings > Server Accounts.
- Click Edit Credentials:
- For each user account, configure the account:
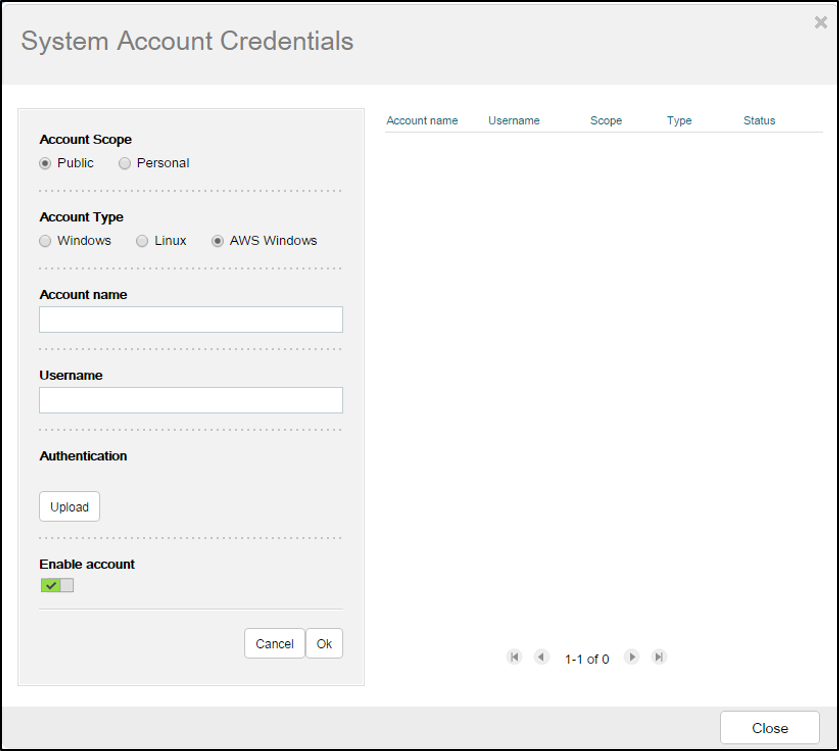
-
Account Type: Whether it should be used for Windows machines or for Linux machines. An additional AWS Windows type is available for convenient access to AWS-native Windows instances.
-
Account name: A descriptive label for the account
-
Username and Password: Local or domain-based user details.
-
Private Key and Private Key Passphrase: For Linux and AWS Windows account types you can select to use an SSH private key instead of a password, in which case you can then Upload an OpenSSH private key file and optionally provide its passphrase.
- JetPatch currently supports private keys in plain and encrypted PEM and PKCS8 formats. Supported key files start with one of the following prefixes: BEGIN RSA PRIVATE KEY, BEGIN ENCRYPTED PRIVATE KEY or BEGIN RSA PRIVATE KEY. Currently key files in the new OpenSSH format, i.e. files that start with BEGIN OPENSSH PRIVATE KEY, are not supported.
For Microsoft Windows instances launched in AWS, if you wish to use the random administrator password generated by AWS, choose 'AWS Windows' account type and upload the SSH private key associated with your AWS Windows instances. JetPatch Agent Manager will ask AWS for an encrypted copy of the random administrator password for each AWS Windows server, and then use the private key to temporarily decrypt this password to access each instance.
For AWS Linux instances: Please note that different operating system images in AWS may use a different username even when sharing the same private key, and so multiple access accounts need to be defined for them. For example, while Red Hat Enterprise Linux instances typically use the ec2-user username, Ubuntu instances tend to use the ubuntu username, and SuSE Linux instances use root as the username. Refer to the AMI details page in AWS for info on the username used with any AMI.
- Click OK.
- Click Close.
To disable an account (for example, before changing a password, to avoid the account being locked due to repetitive login failures), click  . .
|
Comments
0 comments
Please sign in to leave a comment.