Tell Computers to install Locally Publish Updates
Domain-joined clients:
Using the same GPO that you use to set your computers, set the option “Allow signed content from intranet Microsoft update service location” to "enable".
How: Navigate to Computer configuration > Policies > Administrative Templates > Windows Components > Windows Update. Select "Allow signed content from intranet Microsoft update service location" and click Edit policy settings.
Non-domain-joined clients:
Option 1: Configure in bulk using a built-in task
See the endpoint configuration for WSUS steps (note: if you already ran this script before to initially configure the endpoints to WSUS, you can skip this step).
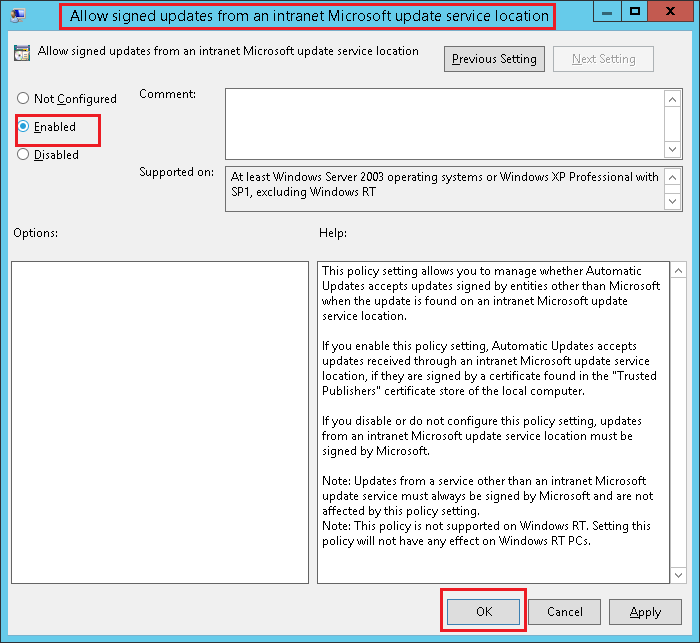
Option 2: Manual Steps
- Open the group policy of the endpoint (start->run->gpedit.msc)
- Configure Updates by going to Computer Configuration -> Administrative Templates -> Windows Components -> Windows Updates ->
- Allow signed updates from an intranet Microsoft update service location -> Enable the policy
Deploy your code signing certificate on Endpoints
Domain-joined clients:
- Create/edit a GPO used to import the certificate (.CER) to all the endpoints in the domain (you should already have this downloaded from the catalog)
- (Computer Config > Windows Settings > Security Settings > Public Key Policies):
Import to both “Trusted Root Certification Authorities” and “Trusted Publishers”
Non-domain-joined clients
Option 1: Configure in bulk using a built-in task
- See the 3rd party patching certificates steps
Option 2: Manual Steps
- Upload the certificate (.CER) to the client (you should already have this downloaded from the catalog)
- Double-click certificate on each client and install to the “Trusted Root Certification Authorities” and “Trusted Publishers”:
Troubleshooting
Note: If you receive a download fail when trying to deploy 3rd party patches via JetPatch activities, it is likely due to certificate issue:
- The WSUS server might lack the proper code-signing certificate (PFX), or
- The clients might not have the certificate (CER) installed correctly into both Trusted Root Certification Authorities and Trusted Publishers.
Comments
0 comments
Please sign in to leave a comment.